How I accidentally found Sensitive data exposure!!
Hello folks, This is Sourav. Hope you are doing awesome on the other side of the screen. I am security enthusiast and a bug bounty hunter from India. Today I will discuss How I accidentally found a sensitive data exposure during my recon.
Okay folks let's get started without wasting any time...
One fine day I was looking for some premium themes for wordpress websites and that's how I landed upon a website which provides all kinds Web Development solutions. Since I am not allowed to reveal the name of the website so will take example.com for the sake of this writeup.
I don't know what came into me but I thought, let's see how secure is a website itself who provides web development solutions to others. If the website is itself safe enough ?? Let's find out..............
I quickly run amass on example.com and started traversing the application to see how it works. Than I noticed that amass quickly completed its operation.
So quickly I took a look at amass output and started looking for live http servers manually one be one each.
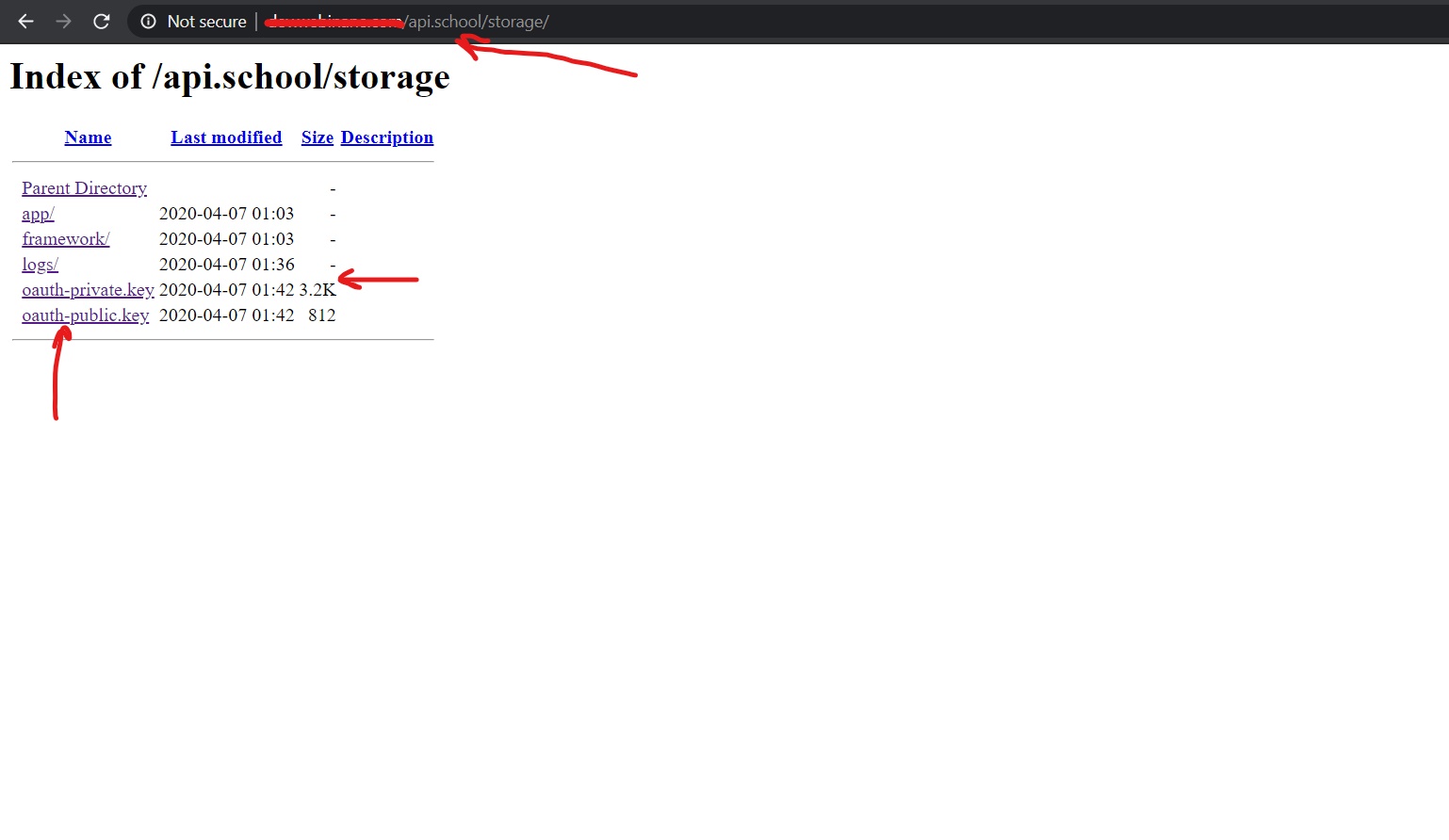
Than this thing caught my eye and I was like ...............
I can also access the laravel logs, Oauth public/private key...................
Now even if this is not enough than let me tell you that I can even download all of this sensitive information along with all of the server side code locally to my computer.
Timeline



Comments
Post a Comment