Hacking Online Classrooms - Part 1
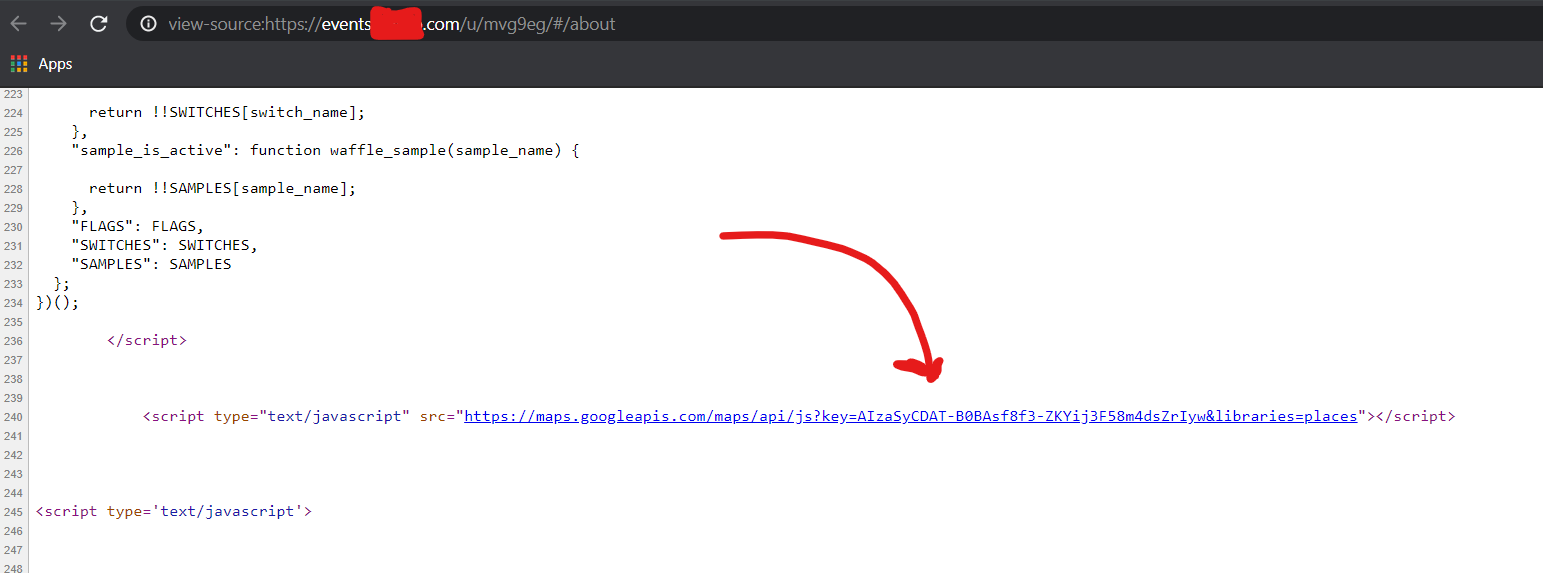
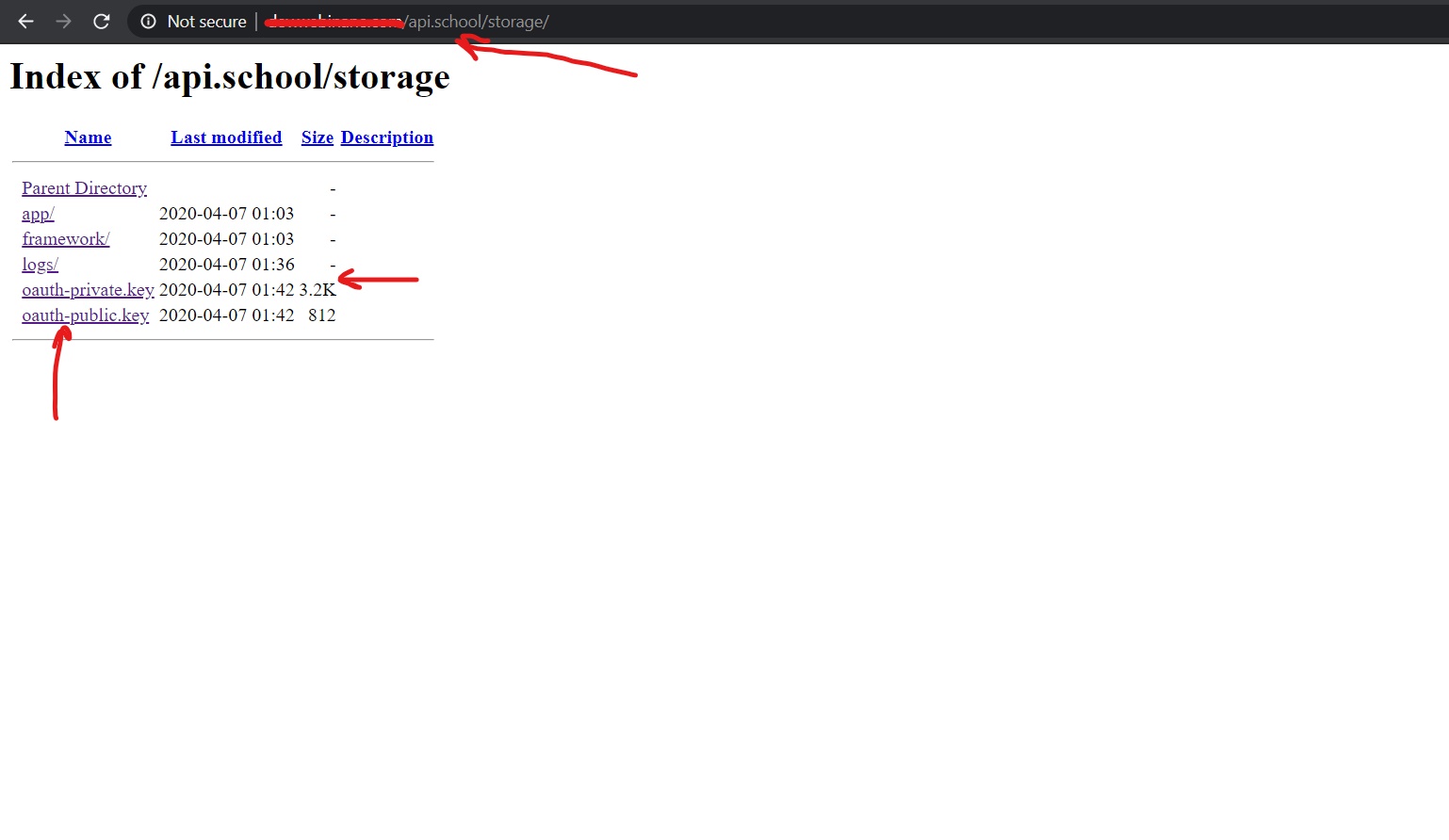
Hello folks, hope you guys are doing awesome. This post is the first part in the series of hacking online classrooms. In this part I will be covering the vulnerabilities I found in one of the Online Classroom. Currently I cannot reveal the name of the classroom so for this blog we will use example.com . I found multiple vulnerabilities in the online classroom example.com but I will discuss some of the coolest ones in this post. Combining Self XSS and CSRF to report Stored XSS ... So in the classroom there is a functionality to create classes. A teacher can create a class and then invite students to his class. So my first instinct to test classroom name for XSS. I created two account one as a teacher and one as a student. From the teacher's account I created a classroom called test from the teacher's account and than joined the classroom from the student's account. Now in the Teacher's account the classroom name test was getting reflected in 3 (Two html context and on...